The Cybersecurity In Wearables Technology Graph is a conceptual map that helps device developers plan, implement, and verify security across wearable ecosystems. By visualizing data flows, device layers, and external interfaces, the Cybersecurity In Wearables Technology Graph supports more resilient products from the first design sketch to field updates.
Understanding the Cybersecurity In Wearables Technology Graph
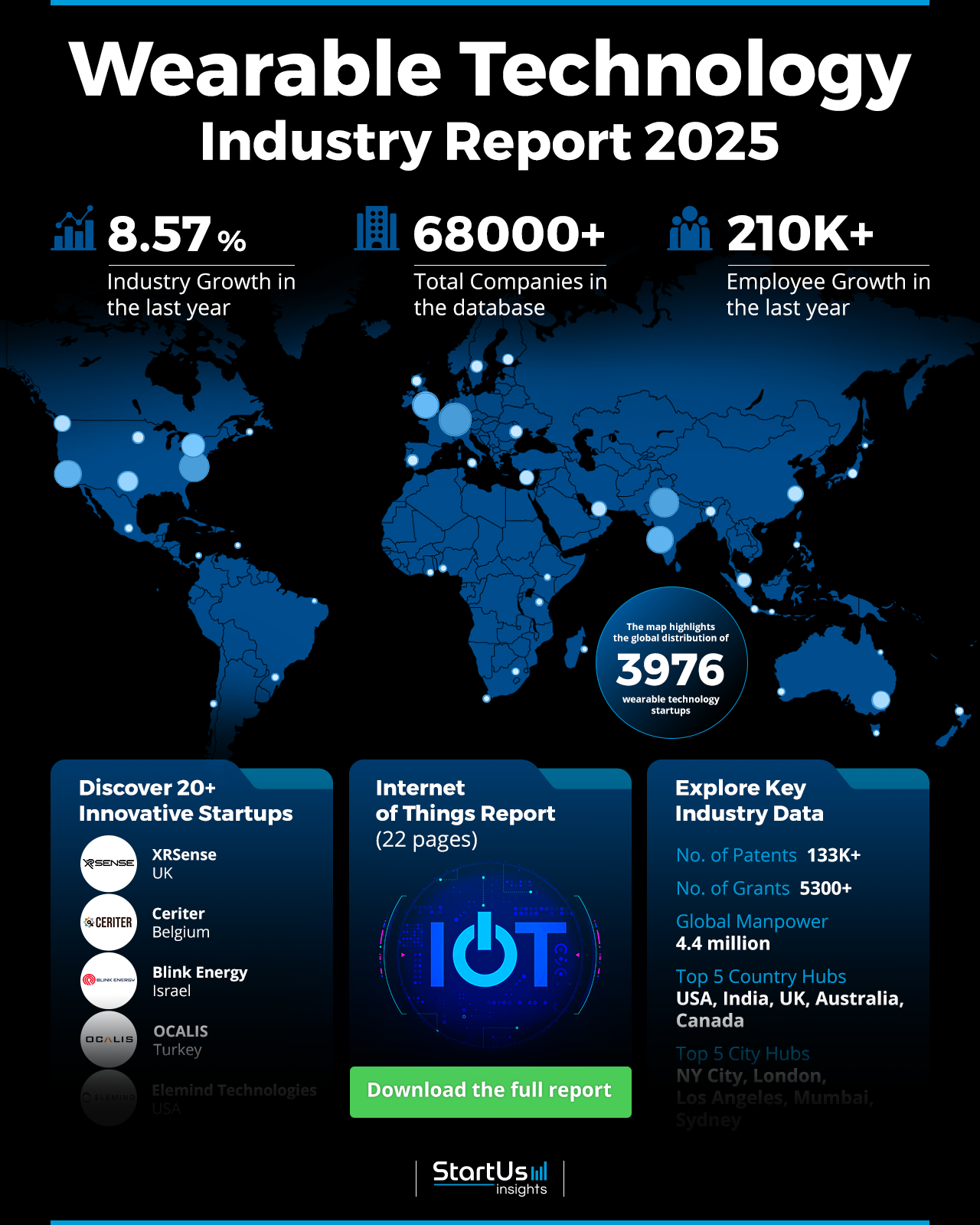
In wearables, data moves from sensors to processors, mobile apps, and cloud services. The Cybersecurity In Wearables Technology Graph provides a framework to track where data is stored, how it is transmitted, who can access it, and which controls are needed at each step. The graph emphasizes security by design, privacy by default, and continuous risk assessment as the product evolves.
Key Components of the Graph
The graph typically includes nodes for data sources (sensors), processing units (on-device and edge), transmission channels (BLE, NFC, Wi‑Fi, cellular), storage locations, and endpoints (mobile apps, cloud services). Edges represent data flow, control signals, and trust relationships. Each node is annotated with security requirements such as encryption, authentication, and access policies.
Key Points
- Map every data flow in the wearable lifecycle to specific security controls and verification tests.
- Account for unique wearables surfaces, including sensors, companion apps, and cloud integrations, when modeling risk.
- Incorporate privacy-by-design and least-privilege principles directly into the graph structure.
- Use threat modeling to prioritize mitigations based on likelihood and impact within constrained device resources.
- Plan for secure updates and hardware-backed key management to maintain trust over the device lifecycle.
Applying the Graph in Device Development
Device developers can embed the Cybersecurity In Wearables Technology Graph into their SDLC by aligning requirements, design reviews, and testing activities with graph nodes. Start with a data catalog that documents what is collected, how it is used, and where it is stored. Then map controls to each data path and define acceptance criteria for both security and privacy outcomes.
Practical steps include threat modeling at early prototypes, threat-informed tests during integration, and continuous monitoring once the product ships. The goal is to create a traceable security narrative from hardware sensors to cloud analytics that can be reviewed by engineers, product managers, and auditors.
Benefits for Device Developers
Using the Cybersecurity In Wearables Technology Graph helps teams identify gaps before they become incidents, reduces rework by clarifying accountability, and supports compliance with data protection regulations. It also fosters a culture of proactive security where trade-offs between usability and protection are made with full visibility.
What is the Cybersecurity In Wearables Technology Graph and how can device developers use it?
+The Cybersecurity In Wearables Technology Graph is a conceptual model that maps data flows, security controls, and trust relationships across the wearable ecosystem. Device developers can use it to plan defense-in-depth, prioritize mitigations for the most exposed paths, and establish traceable security requirements from sensor to cloud. Start by cataloging data, defining data flows, and annotating nodes with concrete controls such as encryption, authentication, and access management.
Which data streams are most at risk in wearables and how can they be secured?
+Primary risks arise at sensor interfaces, on-device storage, wireless transmission, and mobile/cloud endpoints. Security can be enhanced by encrypting data at rest and in transit, implementing mutual authentication across devices and apps, using secure boot and hardware-backed keys, and enforcing strict access controls for companion apps and cloud services.
How does the graph help in threat modeling and risk assessment?
+The graph provides a visual map of data paths and trust boundaries, enabling teams to identify single points of failure, surface areas with weak cryptography, and potential bypass routes. It supports structured risk scoring by assessing likelihood and impact for each node and edge, guiding resource allocation toward the highest-risk paths.
What practical steps should developers take to implement the graph in the SDLC?
+Start with a data inventory and threat-modeling workshop. Create a graph model for the current architecture, then iterate with security reviews at each milestone. Embed security requirements in design artifacts, implement test plans tied to graph nodes, and establish continuous monitoring and incident response aligned with the graph's trust boundaries.
Can the Cybersecurity In Wearables Technology Graph adapt to new wearable categories?
+Yes. The graph is designed to be extensible. New data types, interfaces, and cloud services can be appended as nodes and edges, with updated security controls and trust relationships. Regularly revisiting the graph ensures protection grows alongside hardware and software innovations in wearables.